NETGEAR SRX5308
Введение
Беспроводные маршрутизаторы, сетевые хранилища, IP-камеры, коммутаторы, тонкие клиенты и даже антивандальные ящики – все они уже становились объектом нашего внимания. Однако специализированные устройства сетевой безопасности в нашу тестовую лабораторию попадают впервые. Конечно, разработчики сетевого аппаратного обеспечения задумываются об устойчивости их продукции к взлому и даже иногда наделяют маршрутизаторы и коммутаторы функциями брандмауэра. Сегодня в нашей лаборатории специализированное сетевое устройство, позволяющее защитить узлы, расположенные за ним; балансировать нагрузку и предоставлять отказоустойчивый доступ в глобальную сеть, - NETGEAR SRX5308 – брандмауэр с четырьмя гигабитными LAN-портами и таким же количеством WAN-портов для подключения к операторам. Рассмотрим его подробнее.
Внешний вид
NETGEAR SRX5308 выполнен в металлическом корпусе, габариты которого составляют 330х43х209 мм. Брандмауэр может быть размещён как в стойке, так и на столе.

На одной боковой поверхности расположены вентиляционные отверстия, а за другой размещается вентилятор.


Верхняя крышка содержит лишь объёмное название производителя, а на днище присутствует наклейка с краткой информацией об устройстве и места для резиновых ножек.

Задняя сторона содержит разъём для подключения питания с выключателем, Кенсингтонский замок, порт DB-9 для консольного управления и утопленная кнопка Factory Defaults для сброса пользовательских настроек.

На лицевой панели размещаются восемь портов Gigabit Ethernet: четыре LAN и четыре WAN порта со световыми индикаторами состояния их работы. Общее состояние SRX5308 отображается при помощи двух световых индикаторов: Power и Test. Также на лицевой панели расположено название модели и фирмы-производителя.

Заглянем теперь внутрь устройства.
Аппаратная платформа
Электронная начинка SRX5308 состоит из трёх текстолитовых плат. Одна из них вспомогательная и предназначена для вывода световой индикации на переднюю панель устройства.
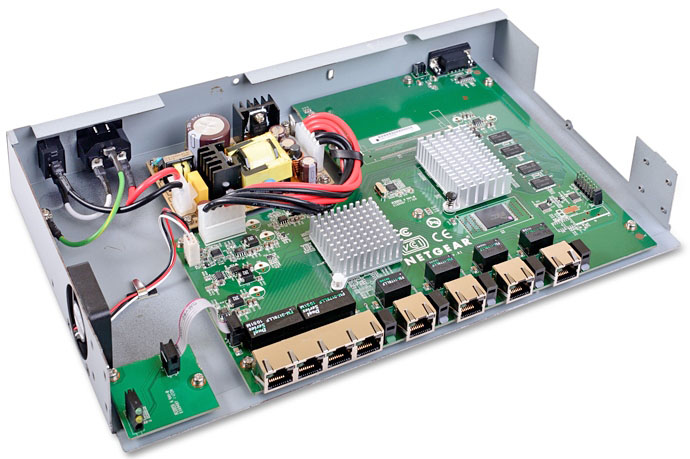
Вторая плата выполняет функции блока питания.
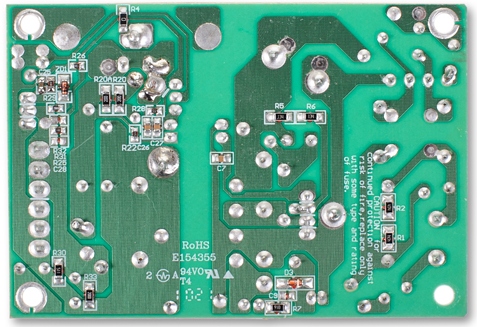
На основной плате практически все элементы располагаются с одной стороны. Исключение составляет лишь интегральная микросхема NXP LVC373A.
Функции коммутатора выполняет Broadcom BCM53118KQLEG с девятью гигабитными портами, блок-схема работы которого представлена ниже.
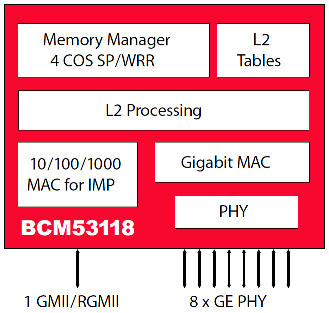
Из приведённой выше схемы следует, что SRX5308 не сможет продемонстрировать скорости маршрутизации более 1 Гбит/с, так как для этих целей требуется передать трафик через процессор, интерфейс с которым имеет пропускную способность всего 1 Гбит/с. При дуплексной передаче 1 Гбит/с – максимальная суммарная скорость передачи в обоих направлениях.
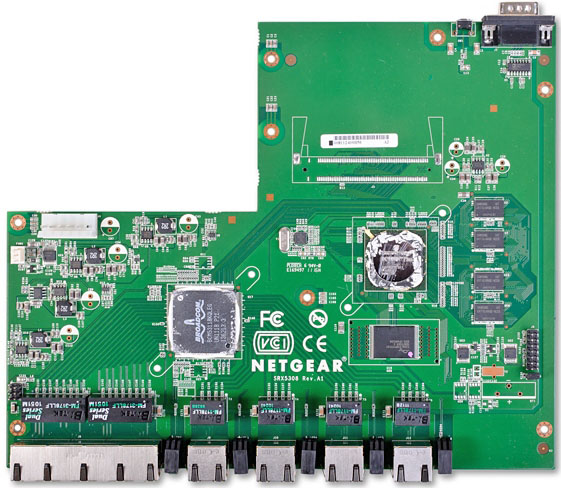
В качестве центрального процессора использован одноядерный чип OCTEON Plus CN5010-700BG564-SCP-G с частотой 700 МГц, блок-схема которого представлена ниже.
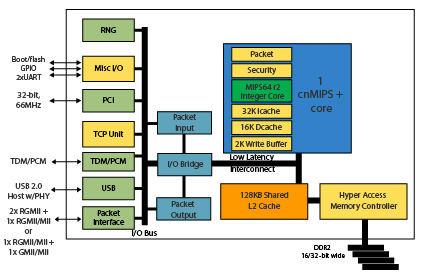
Оперативная память представлена четырьмя DDR2 модулями Samsung K4T1G164QE-HCE6, объём каждого из них равен 128 Мбайт, то есть общий объём оперативной памяти равен 512 Мбайт. Флеш память – Spansion S29GL512P11TFI01 с объёмом 64 Мбайта.
Краткий экскурс в аппаратную начинку SRX5308 мы на этом завершаем, перейдём к программной составляющей.
Обновление прошивки
Обновление прошивки NETGEAR SRX5308 производится с помощью пункта Settings Backup & Upgrade меню Administration веб-интерфейса, где необходимо выбрать файл с новой версией микропрограммного обеспечения и нажать кнопку Upgrade.
Весь процесс обновления занимает порядка четырёх минут.
К сожалению, на данный момент система управления сетевым оборудованием NETGEAR NMS200 не поддерживает SRX5308, поэтому централизованное обновление микропрограммного обеспечения в обсуждаемых брандмауэрах затруднено.
Обзор веб-интерфейса
Доступ к веб-интерфейсу NETGEAR SRX5308 может быть осуществлён с помощью большинства современных браузеров, правда, для некоторых требуется включить поддержку устаревших схем шифрования. Например, в Firefox требуется обратиться к специальной странице about:config и принять всплывающее сообщение. Среди настроек выбрать security.ssl3.dhe_rsa_des_sha и изменить значение на true. Данная особенность присутствует только в устройствах, поставляемых в Россию, и связана с отключенной по умолчанию функцией шифрования данных с применением криптостойких алгоритмов. Обновив прошивку и задействовав тем самым стандартные криптографические алгоритмы (включая SSL), можно подключаться уже без ухищрений.
При входе необходимо указать логин и пароль, которые по умолчанию равны admin и password соответственно.
Подобная цветовая схема уже встречалась нам и в других продуктах NETGEAR, например, коммутаторе GS108PE. После входа пользователь попадает на страничку Monitoring-Router Status-Router Status. Все пункты и подпункты меню расположены в верхней части странички.
Изучим наиболее интересные возможности веб-интерфейса SRX5308.
Подпункт WAN Settings меню Network Configuration содержит вкладку WAN, с помощью которой администратор может произвести настройку каждого из четырёх WAN-интерфейсов брандмауэра. Поддерживаются статические IP-адреса, динамическая настройка с помощью DHCP, PPPoE и PPTP. Как заверяет производитель, в ближайшее время будет также добавлен популярный в России протокол L2TP. Кроме указанных параметров, на интерфейсе может быть настроено также несколько вторичных IP-адресов.
Вкладка WAN Mode позволяет включать или отключать NAT, а также выбирать способ использования нескольких WAN-портов – балансировка или отказоустойчивость.
Балансировка на основе типа трафика может быть настроена с помощью подпункта Protocol Binding. Так, например, голосовой трафик может быть передан через WAN1 интерфейс, тогда как для всех остальных типов будет выбран интерфейс WAN2.
Для каждого внешнего интерфейса может быть настроена регистрация на серверах динамических DNS для сервисов Dynamic DNS, DNS TZO, DNS Oray и 3322 DNS.
Вкладки подпункта LAN Settings позволяют управлять виртуальными сетями и IP-адресами SVI-интерфейсов, параметрами DHCP-сервера для подключенных к LAN-портам узлов, а также группами узлов. Помимо упомянутых возможностей подпункт LAN Settings позволяет администратору вести учёт трафика, потребляемого определёнными узлами.
При необходимости администратор может разместить определённый узел в демилитаризованной зоне, для чего ему потребуется обратиться к подпункту DMZ Setup, где указать дополнительные параметры размещаемого сервера.
Настройки статической и динамической маршрутизации собраны в подпункте Routing. Нам кажется удивительным отсутствие поддержки других протоколов динамической маршрутизации, например OSPF, в таком устройстве.
Управление качеством обслуживания производится с помощью подпункта QoS.
Перейдём теперь к рассмотрению возможностей подпунктов и вкладок пункта Security.
Определить сервисы, профили качества обслуживания и IP-группы можно с помощью вкладок подпункта Services. Такое определение необходимо для удобства конфигурирования брандмауэра. Также SRX5308 позволяет определить до трёх различных расписаний, по которым будут применяться те или иные правила, соответствующая настройка доступна в подпункте Schedule.
Для управления правилами доступа к LAN, WAN и DMZ сегментам необходимо обратиться к первым трём вкладкам подпункта Firewall.
Дополнительные параметры фильтрации и ограничения сессий для протоколов транспортного уровня доступны администраторам во вкладках Attack Checks, Session Limit и Advanced.
Фильтрацией передачи данных на основе MAC-адресов можно управлять с помощью подпункта Address Filter. Также здесь присутствует возможность статической привязке MAC и IP-адресов.
Настройка ограничений скорости для определённых профилей производится в подпункте Bandwidth Profile.
Правила контентной фильтрации доступны в подпункте Content Filtering.
Создание, редактирование и удаление туннелей IPSec и SSL производится с помощью подпунктов и вкладок пункта VPN. Стоит отметить, что SRX5308 для туннелей IPSec поддерживает как режим клиента, так и Site-to-site подключения. Кроме того брандмауэр может обращаться к удалённому RADIUS-серверу для аутентификации подключающихся пользователей.
Управление локальными пользователями и группами производится с помощью пункта Users.
С помощью подпунктов пункта Administration можно управлять доступом к устройству по протоколам HTTPS, telnet и SNMP, сохранять/восстанавливать пользовательские настройки, обновлять прошивку, а также выполнять синхронизацию времени с удалёнными NTP-серверами.
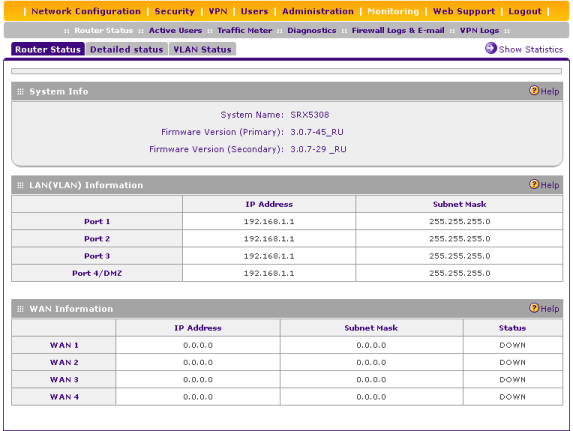
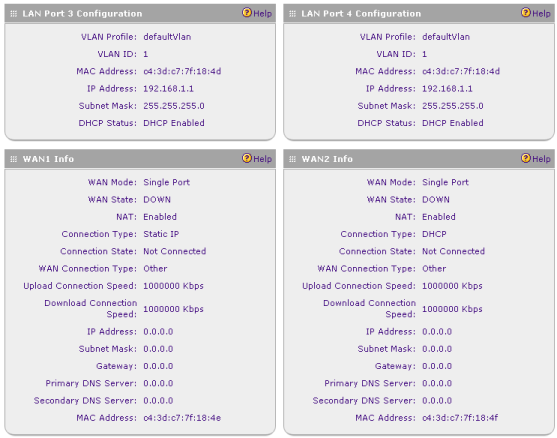
Подпункт Router Status пункта Monitoring отображает краткую информацию о самом устройстве, детализированные сведения о физических портах и интерфейсах виртуальных сетей.
Для каждого из четырёх WAN-портов может быть настроено ограничение и подсчёт потребления трафика в месяц. Соответствующая настройка доступна в подпункте Traffic Meter.
При возникновении различных сетевых проблем администратор может обратиться к подпункту Diagnostics для выполнения ряда диагностических действий.
Доступ к документации и базе знаний по обсуждаемому продукту можно получить с помощью подпунктов пункта Web Support.
Обзор возможностей веб-интерфейса на этом завершается.
Обзор интерфейса командной строки
Доступ к командной строке по протоколу Telnet со стороны LAN-интерфейсов присутствует всегда, его невозможно отключить через веб-интерфейс. Единственное, с помощью браузера можно управлять доступом к командной строке через WAN-интерфейсы. Итак, приступим. Логин и пароль такие же, как и для веб-интерфейса.
SRX5308 login: admin
Password:
********************************************************************************
Welcome To The Netgear SRX5308 Command Line Interface
********************************************************************************
SRX5308$ help
Invalid number of arguments(less)
help <command>
SRX5308$
К сожалению, производитель не предоставляет никакого руководства по командной строке SRX5308, а устроена она, мягко говоря, своеобразно, - человеку, привыкшему к Cisco-подобным командным строкам, придётся переучиваться. С помощью команды ls администратор может получить список команд и их групп.
SRX5308$ help ls
Lists the available commands and groups in the current heirarchy
SRX5308$ ls
admin/ netConf/ cliErrno help verbose saveConfig
bwLimit/ vpn/ cls ls ping
fw/ alias exit pwd reboot
monitor/ cd fileExec script resetConfig
SRX5308$ pwd
/
Переход между группами осуществляется с помощью вызова cd.
SRX5308$ cd admin
admin$ ls
ExternDbStatus/ remoteMgmt/ firmStatus
ExternalAuth/ snmp/ loginTimeoutGet
externUserDb/ sslLocalUserdbStatus/ loginTimeoutSet
language/ sslvpn/ resetConfig
localDbStatus/ timezone/ saveConfig
regionFlag/ userdb/
Группа admin позволяет управлять пользователями и их группами, процедурами аутентификации и временами простоя управляющих сессий, доступами по протоколам HTTP(s), telnet, SNMP; синхронизацией времени; получать информацию об используемой прошивке, а также сохранять произведённые изменения.
admin$ cd remoteMgmt/
remoteMgmt$ ls
config show tr69ConfSet tr69Show
remoteMgmt$ show
<shttpStatus> <shttpAccessType> <shttpStartAddr> <shttpEndAddr> <shttpPort> <act
iveWan> <telnetStatus> <telnetAccessType> <telnetStartAddr> <telnetEndAddr>
1 0 0.0.0.0 0.0.0.0 443 - 0 0 0.0.0.0 0.0.0.0
remoteMgmt$ tr69Show
0 - - - tr-069 tr-069 dps dps 0 127.0.0.1 user passwd
admin$ cd snmp/sysInfo/
sysInfo$ ls
config show
sysInfo$ show
admin netgear SRX5308
admin$ cd timezone/
timezone$ ls
config get rebootTimeSet
timezone$ get
<status> <timezone> <daylight> <ntpmode> <manualtimeset> <hour> <minutes> <secon
ds> <day> <month> <year> <useDefServers> <primaryServer> <secondaryServer> <stra
tum> <vpnpolicy> <reSyncNtpVal> <reboottime> <time>
1 33 0 0 0 0 0 0
0 0 0 1 time-f.netgear.com time-g.netg
ear.com 10 0 120 946877041
Current Time: Mon Jan 03 08:23:21 GMT+0300 2000
admin$ firmStatus
<primary_version> <secondary_version>
3.0.7-45_RU 3.0.7-29_RU
admin$ loginTimeoutGet
<timeout> <domainName>
5
admin$ loginTimeoutSet timeout 10 domainName geardomain
admin$ loginTimeoutGet
<timeout> <domainName>
10 geardomain
Группа bwLimit предназначена для управления доступной полосой пропускания.
SRX5308$ cd bwLimit/
bwLimit$ ls
add edit pktDrpCntShow status
delete pktDrpCntShow show statusGet
bwLimit$ pktDrpCntShow
<packetDropCount>
0
bwLimit$ statusGet
Bandwidth Profiling Status
0
bwLimit$ add test
invalid input argument - test
add <bwProfName - STRING>
<bwMinBw0 - INT>
<bwMaxBw0 - INT>
<bwMinBw1 - INT>
<bwMaxBw1 - INT>
<bwType - INT>
<bwInst - INT>
<bwDirection - INT>
Управление правилами брандмауэра, привязкой MAC и IP-адресов, параметрами определения атак, а также качеством обслуживания и UPnP производится с помощью команд группы fw.
SRX5308$ cd fw
fw$ ls
alg/ ipGrp/ mac/ qos/ sched/ upnp/
groups/ ipMacBind/ ptrgr/ rules/ svc/ web/
fw$ cd alg
alg$ ls
statusGet statusSet
alg$ stat
statusGet statusSet
alg$ statusGet
<algName> <algStatus>
sip 1
fw$ cd ipMacBind/
ipMacBind$ ls
add edit enable
delete emailLogStatusGet ipMacTblGet
disable emailLogStatusSet pktDropCountGet
ipMacBind$ add
error: Invalid argument
ipMacBind$ add test
invalid input argument - test
add <ipMacBindName - STRING>
<status - INT>
<ipAddr - IPV4ADDR>
<mac - STRING>
<logEnable - INT>
fw$ cd rules/
rules$ ls
attackChecks/ conntrack/ dmzWan/ lanDmz/ lanWan/
fw$ cd upnp
upnp$ ls
confSet confShow portMapShow
upnp$ confShow
UPnP Configuration Settings
---------------------------------------------------
Status | ADV Period | TTL
---------------------------------------------------
0 | 30 | 4
fw$ cd web/
web$ ls
keyword/ trustedDomain/ blockWebComp status
web$ status
Display the status of web components blocking
Block Web proxy : 0
Block Java : 0
Block Activex : 0
Block cookies : 0
Группа monitor предоставляет администратору доступ к журнальной информации и данным встроенного счётчика трафика, а также к набору диагностических команд, среди которых присутствуют вызовы tcpdumpStart и tcpdumpStop, позволяющие перехватывать проходящий трафик.
SRX5308$ cd monitor/
monitor$ ls
diag/ firewallLogs/ trafficMtr/ vpnLogs/
monitor$ cd diag/
diag$ ls
arpDel nsLookup reboot tcpdumpStart traceRoute
arpShow ping routeDisplay tcpdumpStop
diag$ routeDisplay
<interface> <dst> <mask> <gw> <metric>
defaultVlan 192.168.1.0 255.255.255.0 0.0.0.0 0
Настройки сетевых интерфейсов SRX5308 представлены в группе netConf, а управление виртуальными частными сетями производится с помощью группы vpn.
netConf$ ls
dmzSetup/ lanGrps/ netQos/ vlan/
duplex/ lanSetup/ routing/ wan/
netConf$ cd lanSetup/
lanSetup$ cd lanStatic/
lanStatic$ pwd
/netConf/lanSetup/lanStatic/
lanStatic$ ls
ifConf ifLShow ipAConf ipAEdit ipAShow
ifDel ifShow ipADel ipALShow
lanStatic$ ifShow
2 1 192.168.1.1 255.255.255.0
0 0 10.1.1.2 255.255.255.0
netConf$ cd vlan/
vlan$ ls
lanmeter/ vDefaultPortConf vlanDel
macPool/ vProfDisable vlanListShow
vConf vProfEnable vlanShow
vConfEdit vlanDefaultPortShow
vlan$ vlanListShow
<profileId> <vlanProfName> <port1Status> <port2Status> <port3Status> <port4Statu
s> <port5Status> <port6Status> <vlanProfstatus> <macAddr>
1 defaultVlan 1 1 1 1 - - 1 c4:3d:c7:7f:18:4d
netConf$ cd /vpn
vpn$ ls
certificate/ modeConfig/ policies/ xauth/
vpn$
Подключение к брандмауэру можно производить также и через консольный порт, функционал которого не отличается от возможностей доступа через telnet.
При загрузке устройства администратор может получить доступ к загрузчику, однако мы не станем останавливаться на его возможностях.
U-Boot 1.1.1 (Development build, svnversion: exported) (Build time: Jan 6 2011 - 16:15:26)
Warning: Board descriptor tuple not found in eeprom, using defaults
CUST_SRX5308 board revision major:2, minor:0, serial #: unknown
OCTEON CN5010-SCP pass 1.1, Core clock: 700 MHz, DDR clock: 200 MHz (400 Mhz data rate)
DRAM: 512 MB
Flash: 64 MB
*** Warning - bad CRC, using default environment
Clearing DRAM....... done
BIST check passed.
Net: octeth0
== Executing bootcmd in 5 seconds - enter ctrl+c to abort 0
SRX5308 bootloader#
Полный журнал загрузки представлен в файле boot.log.
Краткий обзор возможностей командной строки NETGEAR SRX5308 мы на этом завершаем. Упомянем лишь, что команды и группы данного брандмауэра очень похожи на те, что используются в модели FR538G, а документация на это устройство уже содержит описание работы с командной строкой.
Тестирование
Первым тестом, который мы провели над SRX5308, стало установление времени загрузки устройства, под которым мы понимаем интервал времени с момента подачи питания, до получения первого эхо-ответа по протоколу ICMP. NETGEAR SRX5308 загружается за 45 секунд. Мы считаем это нормальным результатом.
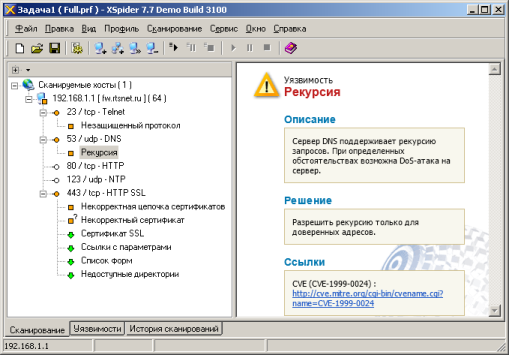
Дальше мы решили проверить защищённость устройства, для чего использовали сканер сетевой безопасности Positive Technologies XSpider 7.7 (Demo build 3100). Сканирование производилось из LAN-сегмента сети. Всего было обнаружено пять открытых портов: TCP-23 (Telnet), UDP-53 (DNS), TCP-80 (HTTP), UDP-123 (NTP), TCP-443 (HTTP SSL). Серьёзных уязвимостей обнаружено не было.
Теперь установим, какие скорости маршрутизации предоставит устройство пользователям. Как мы помним из раздела, посвящённого аппаратной платформе, SRX5308 не сможет продемонстрировать скорости маршрутизации более 1 Гбит/с, поэтому для тестирования мы использовали по одному подключению к LAN и WAN портам устройства. Для тестирования использовалась утилита JPerf 2.0.2, которая создавала один, пять и пятнадцать одновременных TCP-потоков. Продемонстрированные скорости указаны ниже.
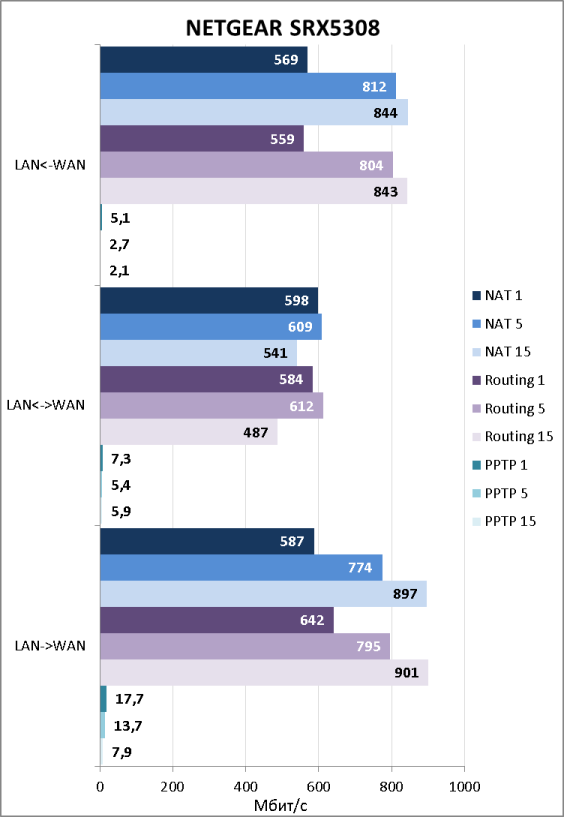
Скорости маршрутизации с использованием PPTP нас, мягко говоря, неприятно удивили. Конечно, мы понимаем, что в корпоративном сегменте доступ в интернет будет предоставляться без использования PPTP, однако столь низкие скорости работы с туннелями являются слабым местом устройства. Естественно, мы сообщили об этом производителю. Оказалось, что в NETGEAR уже работают над этой проблемой и обещали, что в следующей версии прошивки она будет устранена, а скорости маршрутизации через PPTP значительно возрастут.
Нельзя не упомянуть и основные характеристики нашего тестового стенда.
| Компонент | ПК | Ноутбук |
| Материнская плата | ASUS Maximus IV Extreme-Z | ASUS M60J |
| Процессор | Intel Core i7 2600K 3.4 ГГц | Intel Core i7 720QM 1.6 ГГц |
| Оперативная память | DDR3 PC3-10700 Corsair 16 Гбайт | DDR3 PC3-10700 Kingston 8 Гбайт |
| Сетевая карта | Intel 82579V/82583V D-Link DWA-160 |
Atheros AR8131 Atheros AR9285 |
| Операционная система | Windows 7 x64 SP1 Rus | Windows 7 x64 SP1 Rus |
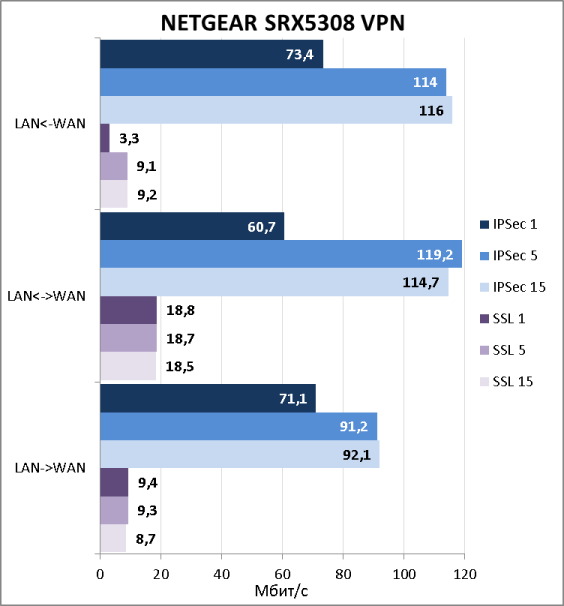
Так как NETGEAR SRX5308 позволяет подключаться удалённым пользователям с использованием SSL-VPN и IPSec-VPN, мы не могли обойти эту возможность стороной. Естественно, мы измерили скорости доступа удалённых пользователей к ресурсам защищаемой локальной сети. Результаты тестов представлены ниже на диаграмме.
Раздел тестирования на этом мы завершаем, подведём итоги.
Заключение
Мы остались довольны гибкостью настроек NETGEAR SRX5308, но некоторые скоростные показатели вызвали у нас недоумение. Использование обсуждаемой модели позволит администратору без затруднений подключить защищаемую локальную сеть средних размеров к интернет с возможностью доступа удалённых пользователей к локальным ресурсам. Сильные стороны брандмауэра перечислены ниже.
-
Гибкость настройки.
-
Простота конфигурации.
-
Устойчивость к сетевым атакам.
-
Возможность организации балансировки по WAN-каналам.
-
Поддержка SSL-VPN.
-
Хорошие скорости IPSec-VPN и маршрутизации.
-
Поддержка виртуальных сетей.
-
Приемлемая цена.
К сожалению, мы не можем не сказать и о недостатках устройства.
-
Веб-интерфейс доступен только на английском языке.
-
Поддержка единственного протокола динамической маршрутизации – RIP.
-
Незначительная заторможенность веб-интерфейса.
-
Отсутствие документации на командную строку.
-
Невысокие скорости SSL-VPN и неприемлемо низкие скорости PPTP.
На момент написания статьи средняя цена на NETGEAR SRX5308 в интернет-магазинах Москвы составляла 15500 рублей.
Постскриптум
После того как обзор был полностью написан, компания NETGEAR выпустила прошивку новой, четвёртой, серии. Среди нововведений, появившихся в релизе, присутствует поддержка IPv6 и сервера PPTP/L2TP. Естественно, мы решили проверить работоспособность данного функционала и начали с поддержки IPv6.
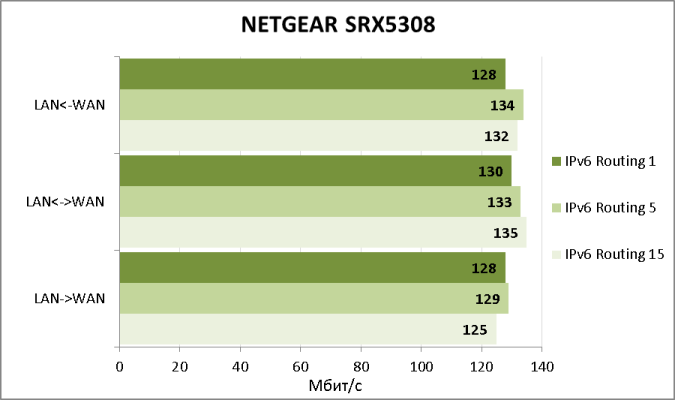
К сожалению, NETGEAR SRX5308 не позволяет выполнять балансировку трафика по WAN-каналам при использовании IPv6. Не обошли стороной мы и скорости маршрутизации для данного протокола.
Далее мы обратились к встроенному серверу PPTP/L2TP и провели измерение скоростей доступа к локальной сети с помощью протокола PPTP.
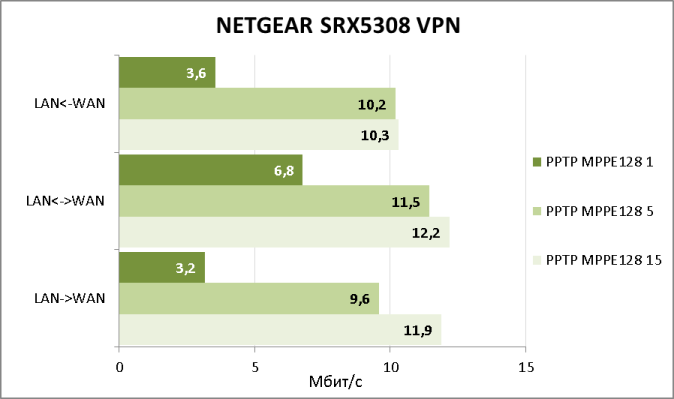
Полученные скорости большими никак не назовёшь. Также мы обнаружили странность в реализации обсуждаемого сервера. Если выбран режим работы NAT, а не Classical Routing в настройках WAN-интерфейса, то тогда все удалённые пользователи, подключающиеся к сети с помощью PPTP для локальных узлов будут видны с одного единственного IP-адреса – адреса LAN-интерфейса устройства и отличить их друг от друга не представляется возможным. Мы надеемся, что в следующих версиях прошивок данная логика работы брандмауэра SRX5308 будет изменена.
